Web/Apache Logs
113 points
Our servers were compromised!! Can you figure out which technique they used by looking at Apache access logs.
flag format: DarkCTF{}
Files
Solution
Found interesting request in given logs:
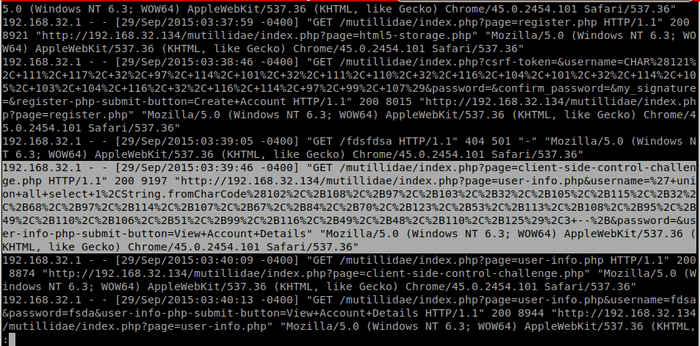
Then combined the charcodes into the flag:
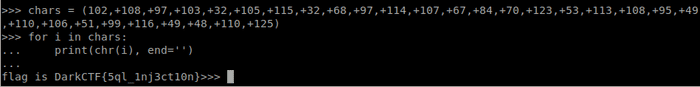
DarkCTF{5ql_1nj3ct10n}