BBomb - Phase 1
Category: Binary Bomb
25 points
Welcome to the CyberDawgs Binary Bomb challenge series! The “bbomb” binary contains a series of mini reversing challenges broken into 9 phases. Each phase becomes incresingly more difficult, but it is not required to solve a phase to move onto the next. Simply press enter for a phase’s input to skip it. Additionally, known phase solutions can be stored in a file named “flags.txt”. See the binary’s welcome message for the format and requirements. When submitting to this scoreboard, wrap the phase’s solution in DawgCTF{}. Happy reversing!
Starting off easy… reversing (things) is fun!
Author: treap_teap
Solution
This is first of ten challenges combined in a chain of Binary Bomb. I must admit that I’ve enjoyed these challenges
the most.
Example execution of the binary:
./bbomb You can store known flags in a file named 'flag.txt' in the same directory as this binary.
Enter 1 flag per line, any empty lines will default to user input, and leave 1 empty line after the last flag. An example to store phase 1, 2, and 4's flags:
----
phAse1_Fl4g
pHA5e2_FLag
phaS34_Fl4g
----
(Note: This file must use Unix line endings. If you edit this file on a Windows machine, run 'dos2unix' on the file)
Welcome to the binary bomb! Tick tock...
To skip a phase, press enter as the phase's input
Flag file 'flags.txt' not found in this directory - using user input.
Starting off easy... reversing (things) is fun! (Wrap all flags in DawgCTF{} when submitting to the scoreboard)
Phase 1 answer: I don't know
Psst... that's the answer to phase 9 :)
Can you help me find my lost key so I can read my string?
Phase 2 answer:
Would you look at that!? The binary bomb went off
Reflections? Rotations? Translations? This is starting to sound like geometry...
Phase 3 answer:
Would you look at that!? The binary bomb went off
This is the phase you have been waiting for... one may say it's the golden stage!
Let's switch things up! Numerical inputs map to line numbers in rockyou.txt, and each word is separated by a '_' (if the phase's solution is 4 5, the flag would be DawgCTF{password_iloveyou})
Phase 4 answer:
Not quite...
Are you really, really ready and excited for this stage?
Phase 5 answer:
___
_/ |\\
/( )| ) )
(_( (_| _))
\|}|)|/
( |)1 )
(0|{ |1\)
Oh no... I lost the key to my string again :(
Phase 6 answer:
Would you look at that!? The binary bomb went off
At least we can say our code is resuable
Phase 7 answer:
So close!
Go touch grass!
Phase 8 answer:
Better luck next time
Who doesn't <3 arrays?
Phase 9 answer:
oof
You've made it to the end, but some phases still remain active!Taking a look into Ghidra gave me overview how it works.
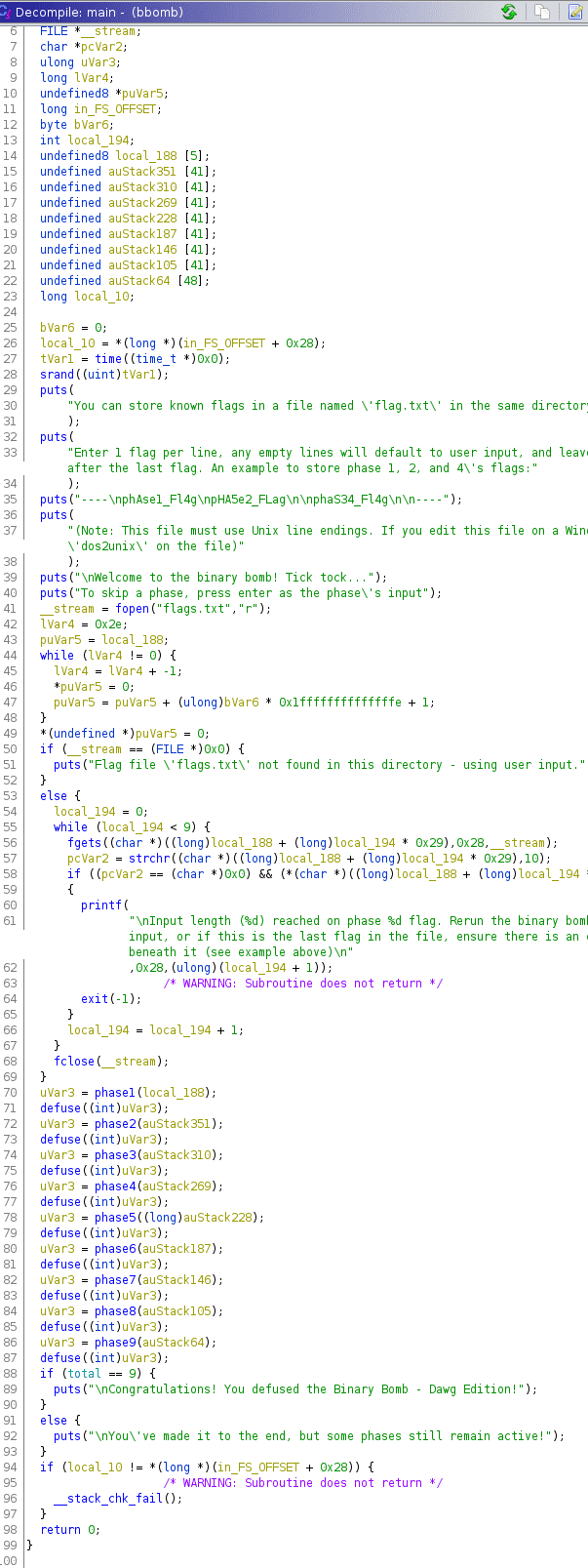
Every challenge seemed to has it’s own phase function.
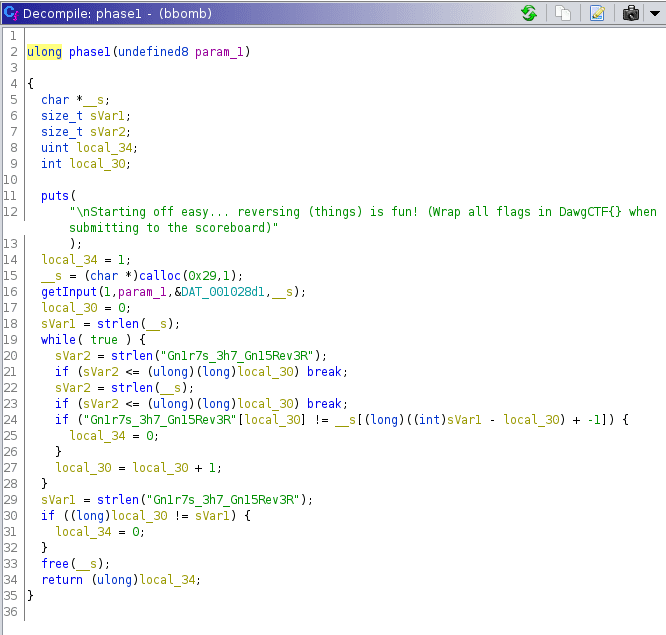
First flag was super easy to find, it was the string in reverse order, found in the decompiled source.
Flag
DawgCTF{R3veR51nG_7h3_s7r1nG}