Profezzor revenge
Category: Crypto
100 points
The Profezzor has sent an encrypted pdf assignment, but he told its easily crackable. Can you guys figure out the assignment, I need to submit it ASAP.
Solution
Provided file looks like a total meaningless mess.
file assignment.txt
assignment.txt: dataxxd assignment.txt | head
00000000: 8baa fef8 83cb 948d a3f0 9f7d 0c39 197d ...........}.9.}
00000010: 2139 29b3 a4cb 9a8e 8e95 d8d4 a3f0 8682 !9).............
00000020: 81aa dbd9 cb89 9a8c 8eca 9aec 8ed5 eec7 ................
00000030: de9f 95fd cf8e dbd2 c19d 8480 a3f0 dfd0 ................
00000040: ca95 d8d4 a3f0 889e 9eda d5dc c4f7 b082 ................
00000050: 92d5 f9d1 db94 ce9e 9fd5 f1d7 ca89 e18d ................
00000060: 8eca 9aec f3d5 eec7 de9f 95ee cf9d dfcd ................
00000070: 90c4 b7b4 cb94 ded1 cc90 b7b4 9dda 8a9e ................
00000080: c198 d0b3 a4c6 8691 ed95 d4ca cb94 cecd ................
00000090: 8ece 9a8e 8ea8 95f3 cb9e d3df ec95 c2e5 ................But, we know it’s encoded pdf. Pdf header usually starts with something like %PDF-1.5\n%. I’ve decided to check if
the file is simply xored by something. To do so, I’ve used first 10 bytes of the file.
from pwn import xor
a = b'\x8b\xaa\xfe\xf8\x83\xcb\x94\x8d\xa3\xf0'
b = b'%PDF-1.5\n%'
xor(a, b)Output:
b'\xae\xfa\xba\xbe\xae\xfa\xba\xb8\xa9\xd5'Can you see the pattern? Repeated AE FA BA BE (byte on 8th position differs but if you check with b'%PDF-1.3\n%' -
it fits).
Let’s try it…
from pwn import xor
key = b'\xae\xfa\xba\xbe'
f1 = open('assignment.txt', 'rb')
f2 = open('assignment.pdf', 'wb')
f2.write(xor(f1.read(), key))
f1.close()
f2.close()And, here’s the flag…
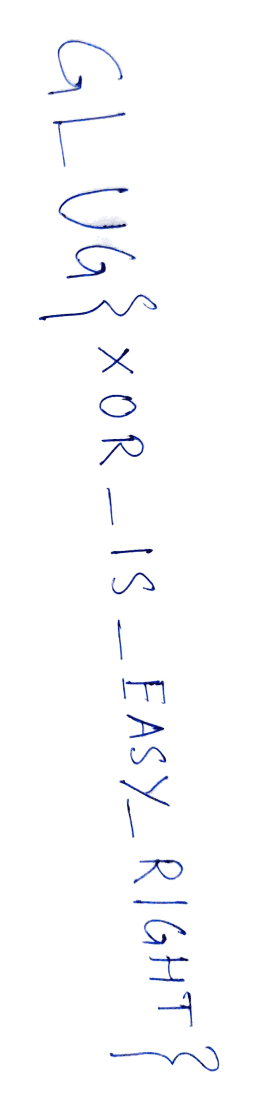
Flag
GLUG{XOR_IS_EASY_RIGHT}