0xSSRF
Category: Web
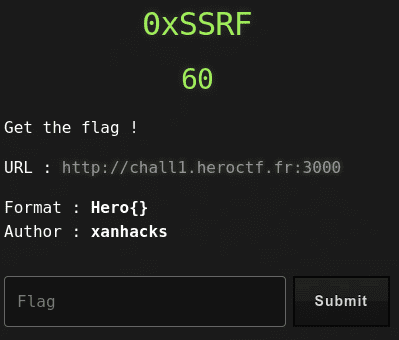
60 points
Get the flag !
URL : http://chall1.heroctf.fr:3000
Format : Hero{}
Author : xanhacks
Solution
Challenge title suggests it’s about server side request forgery. We’ve been given simple webpage which downloads the input url and presents it below the form.
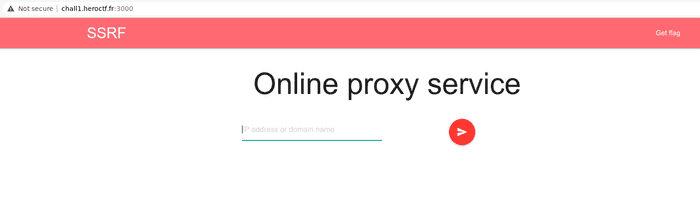
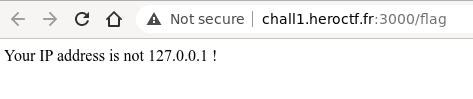
There’s also the link to http://chall1.heroctf.fr:3000/flag which visited gives below response.
The form doesn’t allow to use urls such as localhost or 127.0.0.1, also has input length limit.
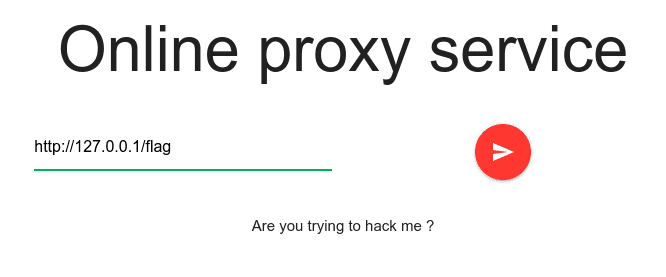
The flag has been conquered by passing http://0:3000/flag input.
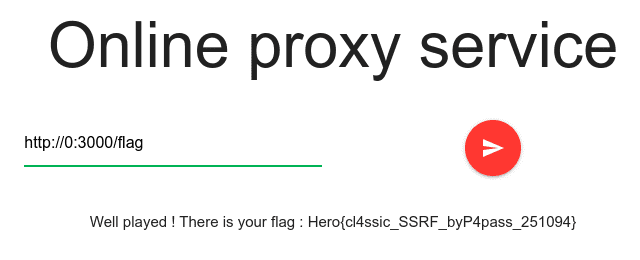
Flag
Hero{cl4ssic_SSRF_byP4pass_251094}