PwnQL #1
Category: Web
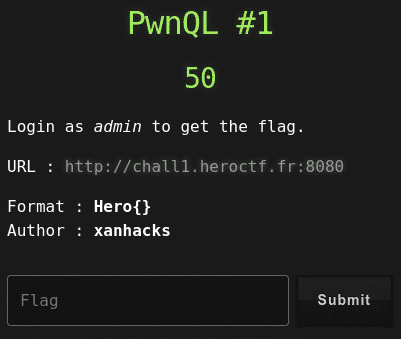
50 points
Login as admin to get the flag.
URL : http://chall1.heroctf.fr:8080
Format : Hero{}
Author : xanhacks
Solution
Name of challenge suggest it’s about SQL injection.

Nothing suspicious, let’s have a look into the source…
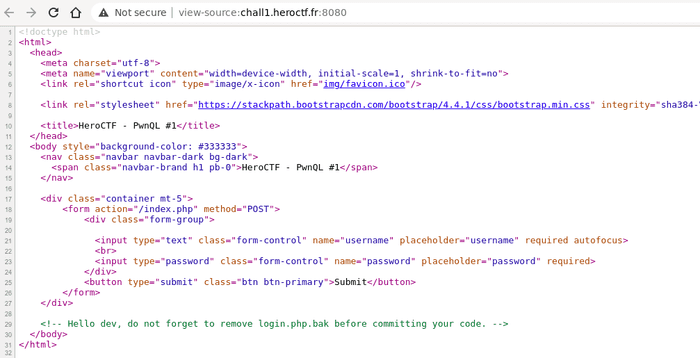
Ok, let’s try to get login.php.bak.
<?php
require_once(__DIR__ . "/config.php");
if (isset($_POST['username']) && isset($_POST['password'])) {
$username = $_POST['username'];
$password = $_POST['password'];
$sql = "SELECT * FROM users WHERE username = :username AND password LIKE :password;";
$sth = $db->prepare($sql, array(PDO::ATTR_CURSOR => PDO::CURSOR_FWDONLY));
$sth->execute(array(':username' => $username, ':password' => $password));
$users = $sth->fetchAll();
if (count($users) === 1) {
$msg = 'Welcome back admin ! Here is your flag : ' . FLAG;
} else {
$msg = 'Wrong username or password.';
}
}Ok, it seems that input data isn’t sanitized in any way and used in the query. Let’s try to login as admin with
password %.
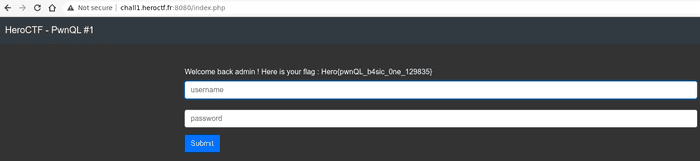
Success! :-)
Flag
Hero{pwnQL_b4sic_0ne_129835}