una acies
Category: Revenge
MEDIUM
Tis an elegant Python poem. Thou shalt not reverse.
Note
Please run the script using Python 2.
una_acies.zip
https://cdn.discordapp.com/attachments/840067093344813097/840069222075858964/una_acies.zip
Connect via
nc acies.sdc.tf 1337
una-acies.py
(lambda __print, __g, __contextlib, __y: (lambda __mod: (lambda __f: type(__f)(type(__f.func_code)(__f.func_code.co_argcount, __f.func_code.co_nlocals, __f.func_code.co_stacksize, __f.func_code.co_flags | __mod.print_function.compiler_flag, __f.func_code.co_code, __f.func_code.co_consts, __f.func_code.co_names, __f.func_code.co_varnames, __f.func_code.co_filename, __f.func_code.co_name, __f.func_code.co_firstlineno, __f.func_code.co_lnotab, __f.func_code.co_freevars, __f.func_code.co_cellvars), __f.func_globals, __f.func_name, __f.func_defaults, __f.func_closure)())(lambda: [[[[[[[[[(lambda __out: (lambda __ctx: [__ctx.__enter__(), __ctx.__exit__(None, None, None), __out[0](lambda: None)][2])(__contextlib.nested(type('except', (), {'__enter__': lambda self: None, '__exit__': lambda __self, __exctype, __value, __traceback: __exctype is not None and (issubclass(__exctype, EOFError) and [True for __out[0] in [(lambda after: after())]][0])})(), type('try', (), {'__enter__': lambda self: None, '__exit__': lambda __self, __exctype, __value, __traceback: [False for __out[0] in [((lambda __after: __y(lambda __this: lambda: (__print('Enter key: ', end=''), (sys.stdout.flush(), [(__print(test(u)), (sys.stdout.flush(), __this())[1])[1] for __g['u'] in [(raw_input())]][0])[1])[1] if True else __after())())(lambda: (lambda __after: __after())))]][0]})())))([None]) for __g['flag'] in [(open('flag.txt').read())]][0] for __g['secret'] in [("7<`+'eX#&QcZ1zVrr2's`%>}B7")]][0] for __g['test'], test.__name__ in [(lambda what: (lambda __l: [[[[('nope', flag)[(why(why(__l['what'], no()), test2()) == secret)] for __l['j'] in [(test2())]][0] for __l['d'] in [(ok(5))]][0] for __l['b'] in [(no())]][0] for __l['what'] in [(what)]][0])({}), 'test')]][0] for __g['why'], why.__name__ in [(lambda a, b: (lambda __l: [''.join([chr((ord(__l['x']) ^ ord(__l['y']))) for (__l['x'], __l['y']) in zip(str(__l['a']), __l['b'])]) for __l['a'], __l['b'] in [(a, b)]][0])({}), 'why')]][0] for __g['no'], no.__name__ in [(lambda : (lambda __l: [(lambda __items, __after, __sentinel: __y(lambda __this: lambda: (lambda __i: [[__this() for __l['k'] in [((__l['k'] | (((__l['a'] * __l['a']) << ((__l['a'] % __l['k']) * __l['a'])) ^ (__l['a'] * __l['k']))))]][0] for __l['a'] in [(__i)]][0] if __i is not __sentinel else __after())(next(__items, __sentinel)))())(iter(range(23)), lambda: str(__l['k']), []) for __l['k'] in [(3)]][0])({}), 'no')]][0] for __g['test2'], test2.__name__ in [(lambda : str(ok(2)), 'test2')]][0] for __g['ok'], ok.__name__ in [(lambda test: (lambda __l: [[(lambda __items, __after, __sentinel: __y(lambda __this: lambda: (lambda __i: [[__this() for __l['x'] in [((__l['x'] | (__l['i'] ^ ((__l['i'] * __l['x']) + __l['x']))))]][0] for __l['i'] in [(__i)]][0] if __i is not __sentinel else __after())(next(__items, __sentinel)))())(iter(range(43)), lambda: __l['x'], []) for __l['x'] in [(5)]][0] for __l['test'] in [(test)]][0])({}), 'ok')]][0] for __g['sys'] in [(__import__('sys', __g, __g))]][0] for __g['print_function'] in [(__mod.print_function)]][0]))(__import__('__future__', __g, __g, ('print_function',), 0)))(__import__('__builtin__', level=0).__dict__['print'], globals(), __import__('contextlib', level=0), (lambda f: (lambda x: x(x))(lambda y: f(lambda: y(y)()))))flag.txt
sdctf{example_flag}Solution
PyCharm debugger was indispensable to solve this challenge. After a while of playing with the code I’ve found some interesting items.
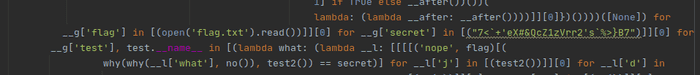
secret
"7<`+'eX#&QcZ1zVrr2's`%>}B7"
no()
'24174820773702277904438513296095994890636308596115538991428195003851059431016851239563801619073548623924767715011378533702776973138621606807751098367'
test2()
'1079734025633873781522191095453466434393488467829981183'
why('a', 'b')
'\x03'
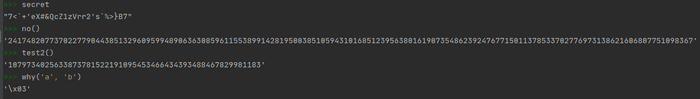
And that was the moment, when I realized why() is actually xor. To find the secret key I had to xor it again.
why(why(secret, test2()), no())
'48f%$n^##Sf^2pSvr3&rf$7qB4'Tried the above as the input…
Enter key: >? 48f%$n^##Sf^2pSvr3&rf$7qB4
sdctf{example_flag}Then once again on remote application…
nc acies.sdc.tf 1337
Enter key: 48f%$n^##Sf^2pSvr3&rf$7qB4
sdctf{r0s3s_R_r3d,V101375_r_blu3,Pyth0n_3ntangl3s,&u_unr4v3l}
Flag
sdctf{r0s3s_R_r3d,V101375_r_blu3,Pyth0n_3ntangl3s,&u_unr4v3l}