Objects
Category: Web Security
200 points
I love mango and i love db too.
Link: https://ch8.sbug.se/
Solution
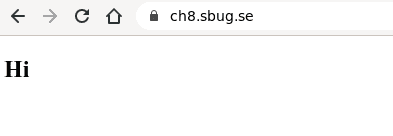
At the beginning I’ve been greeted by this simple page.
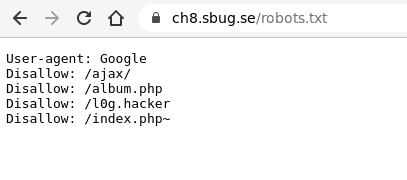
Then I found robots.txt.
Below is the content of l0g.hacker and index.php~.
<?php
if ( $_GET['flag_id'] == $flagid ){ echo $flag; }
/*
u need to get the flag ID, and use this ids ;)
IDs:
5ceb45045c1fa2a0df9f3da7
5ceb749d5c1fa2a0df9f3da8
5ce2bf6c5c1fa2a0df9f3da9
i love mongo remember that.
*/Mon May 27 2019 10:01:40 GMT+0800 (UTC) Start service
Mon May 27 2019 13:24:45 GMT+0800 (UTC) Start database
Sat May 20 2019 22:53:32 GMT+0800 (UTC) Start Updated
Fri May 30 2019 12:46:59 GMT+0800 (UTC) Flag Added HereOk, so it seems that every ID corresponds to database event. The one unknown is for Flag Added Here. So the job in
this challenge is to calculate the ObjectID. I’ve achieved it with two steps.
-
I didn’t understand how IDs are generated, so first of all I’ve installed
pymongoand tried to generate the Object as below (the2019, 5, 30, 4, 46, 59is taken from the logs taking into account the time zone).import bson import datetime bson.ObjectId().from_datetime(datetime.datetime(2019, 5, 30, 4, 46, 59)) - Above gave me an ObjectID
5cef60430000000000000000. It seemed like something was missing here. By something I meant incrementation part. I took5c1fa2a0df9f3da9from the last timestamp. Incremented it by1, which gave me5c1fa2a0df9f3daa. Combined together with my ObjectID gave me5cef60435c1fa2a0df9f3daa.
Going to https://ch8.sbug.se/index.php?flag_id=5cef60435c1fa2a0df9f3daa gave me the flag.
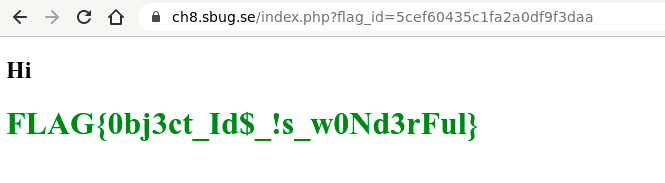
Flag
FLAG{0bj3ct_Id$_!s_w0Nd3rFul}