Cold Compress Inside
Category: Forensics
100 points
Raj wanted to send a huge chunk of data. FInd it
Note : Enclose the flag in ‘SHELL{’ & ’}‘.
file: COLD_COMPRESS.jpg
Solution
After image data there was appended zip archive, I’ve extracted it with binwalk.
binwalk -e COLD_COMPRESS.jpg DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 3840 x 2558, 8-bit/color RGBA, non-interlaced
17158270 0x105D07E Zip archive data, at least v2.0 to extract, compressed size: 18722, uncompressed size: 48441, name: o.exe
17177027 0x10619C3 Zip archive data, at least v2.0 to extract, compressed size: 2987, uncompressed size: 17256, name: o
17180215 0x1062637 End of Zip archive, footer length: 22Archive was not password protected and contained o.exe.
With below I get the list of strings, between which I found one which was the flag.
strings o.exe | less
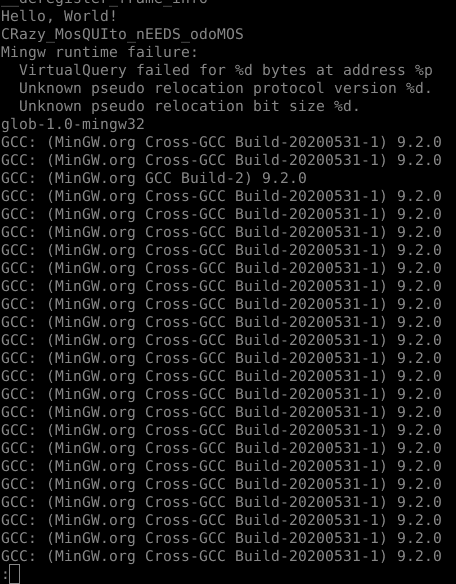
Flag
SHELL{CRazy_MosQUIto_nEEDS_odoMOS}