Misleading Steps
Category: Reverse Engineering
468 points
Misleading Steps often lead you to unexpected places…
file: mislead
Solution
Given file is of course a binary.
file misleadmislead: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64
.so.2, BuildID[sha1]=f74d0c937579d01c4254bb3da72c2d3ee9d5dc96, for GNU/Linux 3.2.0, not strippedDuring execution it types the text letter by letter in some interval.
./mislead The first appearance deceives many,the intelligence of a few perceives what has been carefully hidden...Let’s try to find the flag…
strings mislead | grep vishwavishwaCTF{1_0ft3n_M1sl3ad_pPl}It’s not that easy, given string is not a flag but the mislead mentioned in the name of challenge.
Ok, let’s use ghidra.
There’s an interesting stuff in the assembly code of main.
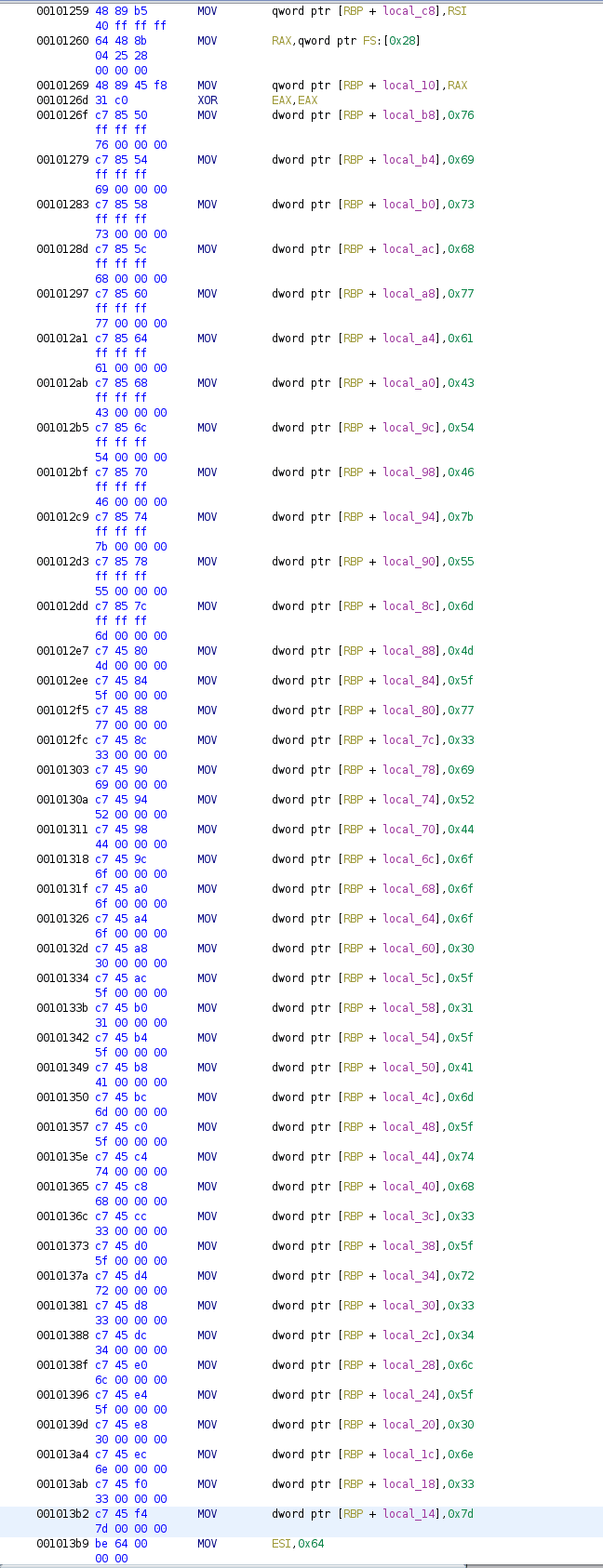
I noted it down as 7669736877614354467b556d4d5f77336952446f6f6f305f416d5f7468335f7233346c5f306e337d and created
python script to decode.
hexcode='7669736877614354467b556d4d5f77336952446f6f6f305f416d5f7468335f7233346c5f306e337d'
flag = ''
for i in range(int(len(hexcode)/2)):
flag = (chr((int(hexcode, 16) >> 8 * i) % 256)) + flag
print(flag)And now I’m think to myself, why I didn’t use xxd? So here’s the alternative.
echo -n 7669736877614354467b556d4d5f77336952446f6f6f305f416d5f7468335f7233346c5f306e337d | xxd -p -rvishwaCTF{UmM_w3iRDooo0_Am_th3_r34l_0n3}Flag
vishwaCTF{UmM_w3iRDooo0_Am_th3_r34l_0n3}