Rotations
Category: Reverse Engineering
450 points
Rotations make you dizzy…don’t they?
file: mm
Solution
Attached file is a binary.
file mmmm: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked,
interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=9d1420344c3a7c70c70b68b947ef2ec8ae498eb1,
for GNU/Linux 3.2.0, not stripped./mm
bla bla bla
EWWWW DUMBBBDecompiled the binary with Ghidra.
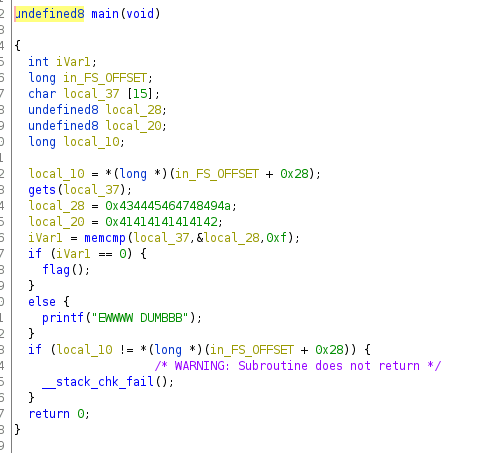
As it is Little Endian, 0x434445464748494a equals to JIHGFEDC and 0x41414141414142 equals to BAAAAAA.
At this moment I skipped flag() investigation (it was not necessary).
./mm
JIHGFEDCBAAAAAA
ivfujnPGS{s1Nt_1f_e0g4gRq_Ol_!3}To sort out this roted flag I wrote python script.
from string import ascii_letters, digits
flag_encoded = 'ivfujnPGS{s1Nt_1f_e0g4gRq_Ol_!3}'
flag_decoded = ''
for c in flag_encoded:
if c not in '{}_' + digits:
if chr(ord(c) + 13) in ascii_letters:
flag_decoded += chr(ord(c) + 13)
elif chr(ord(c) - 13) in ascii_letters:
flag_decoded += chr(ord(c) - 13)
else:
flag_decoded += c
else:
flag_decoded += c
print(flag_decoded)Flag
vishwaCTF{f1Ag_1s_r0t4tEd_By_!3}