Function Pointer Fun
Category: reverse
50 points
Somehow, by means unbeknowst to us, you have access to Melon Eusk’s terminal. But can you crack his password? Rumor is he wrote his own verification algorithm…
nc ctf2021.hackpack.club 10998
File: chal
Solution
The challenge file is a binary.
file chal
chal: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so
.2, BuildID[sha1]=d8a7734793c9b72b532380c335a53ad118c3768e, for GNU/Linux 3.2.0, with debug_info, not stripped./chal
Hello, Mr. Eusk.
Password > No idea what's going on here
Whip a Tesla, spinners lookin' kinda extraAnd it’s not possible to move on without my friend Ghidra ;-)
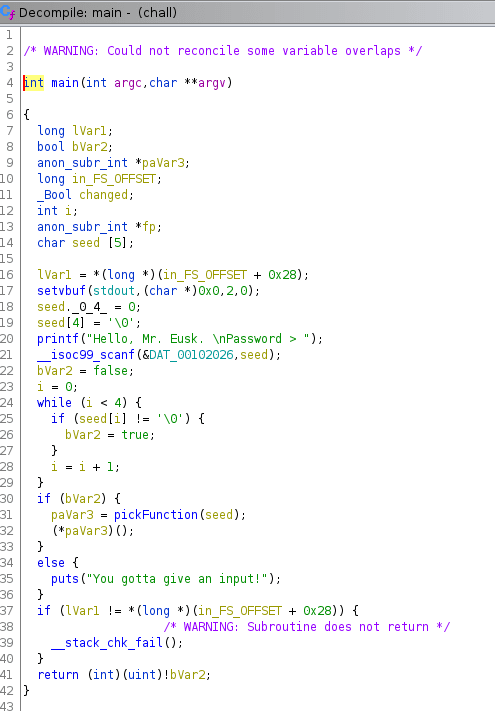
Conclusions after reading the main function:
- password must be 4 characters long,
- then it’s passed to
pickFunctionwhere some more logic happen, let’s take a look there.
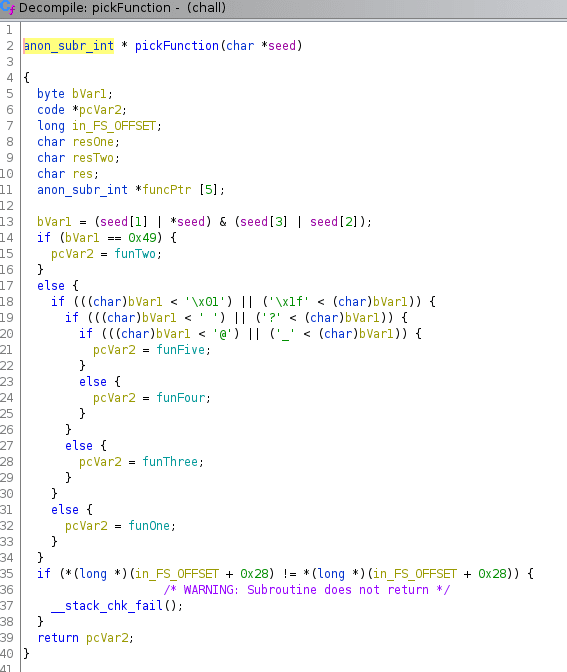
Ok, that’s what I’ve expected, some logic to choose function based on argument. I’ve also checked the decompiled
functions. The only one worth taking a look is funTwo which can print out the flag.
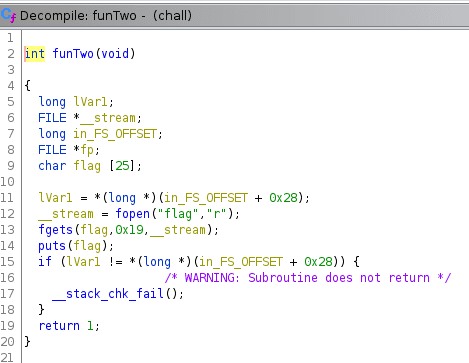
To execute this function (seed[1] | *seed) & (seed[3] | seed[2]) must be equal to 0x49. It means that password input
must be IIII (I is 0x49, so by passing IIII the above operation would look like (0x49 | 0x49) & (0x49 | 0x49)
which equals to 0x49). Let’s check it.
nc ctf2021.hackpack.club 10998
Hello, Mr. Eusk.
Password > IIII
flag{c1RcU1t5_R_fUn!2!}Flag
flag{c1RcU1t5_R_fUn!2!}