FlowRev
Category: Reverse Engineering
500 points
The name of the challenge signifies the method of solving.
file: a.out
Solution
file a.out a.out: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.s
o.2, BuildID[sha1]=a0e015bbe044f88bfcc6544ce015aca480b86641, for GNU/Linux 3.2.0, not stripped./a.out
blahblah433 the number is important..
4+3+3-2 conversion required.
Try again?Ok, time for ghidra…
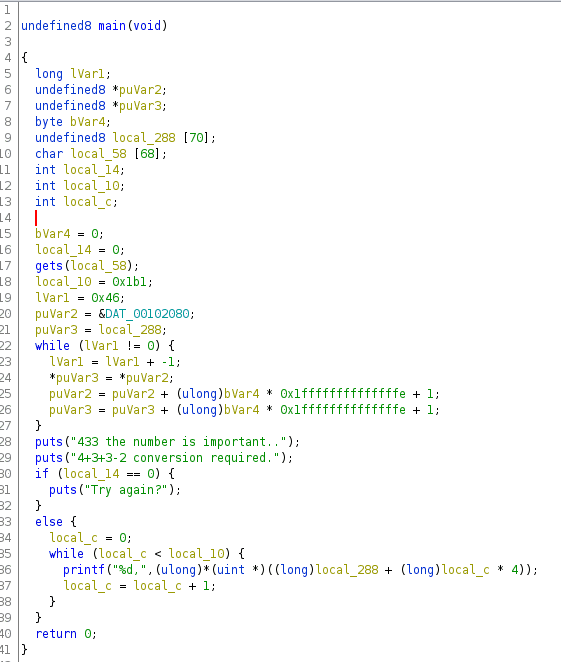
Input seems to be 68 characters long, let’s overflow it.
./a.out
000000000000000000000000000000000000000000000000000000000000000000000433 the number is important..
4+3+3-2 conversion required.
67,66,40,66,71,40,67,63,40,66,70,40,67,67,40,66,61,40,64,63,40,65,64,40,64,66,40,67,142,40,65,65,40,65,146,40,64,144,40,
63,64,40,66,145,40,66,61,40,64,67,40,66,65,40,64,64,40,65,146,40,67,64,40,63,60,40,65,146,40,66,144,40,63,60,40,64,64,40
,63,61,40,66,66,40,65,71,40,65,71,40,65,71,40,65,146,40,65,67,40,63,63,40,66,143,40,66,143,40,65,146,40,66,64,40,63,63,4
0,67,63,40,66,65,40,67,62,40,65,143,40,62,146,40,63,63,40,66,64,40,67,144,808464432,808464432,808464432,808464432,808464
432,808464432,808464432,808464432,808464432,808464432,808464432,808464432,808464432,808464432,808464432,808464432,808464
432,48,433,159,-2066816432,22062,-245445366,32565,1777554504,32765,0,1,-2066816631,22062,-245446705,32565,0,0,493869473,
-359893113,-2066816864,22062,0,0,0,0,0,0,2131745185,-1188319748,1078581665,-1195729753,0,0,0,0,0,0,1,0,1777554504,32765,
1777554520,32765,-243408512,32565,0,0,0,0,-2066816864,22062,1777554496,32765,0,0,0,0,-2066816818,22062,1777554488,32765,
28,0,1,0,1777558111,32765,0,0,1777558119,32765,1777558135,32765,1777558213,32765,1777558232,32765,1777558252,32765,17775
58310,32765,1777558354,32765,1777558399,32765,1777558440,32765,1777558463,32765,1777558525,32765,1777558558,32765,177755
8577,32765,1777558605,32765,1777558620,32765,1777558642,32765,1777558654,32765,1777558691,32765,1777558712,32765,1777558
764,32765,1777558797,32765,1777558844,32765,1777558877,32765,1777558952,32765,1777558967,32765,1777558984,32765,17775605
03,32765,1777560756,32765,1777560787,32765,1777560821,32765,1777560838,32765,1777560890,32765,1777560966,32765,177756099
0,32765,1777561013,32765,1777561033,32765,1777561057,32765,1777561066,32765,1777561077,32765,1777561085,32765,1777561096
,32765,1777561113,32765,1777561144,32765,1777561174,32765,1777561309,32765,1777561371,32765,1777561399,32765,1777561453,
32765,1777561488,32765,1777561557,32765,1777561567,32765,0,0,33,0,1778188288,32765,16,0,-1075053569,0,6,0,4096,0,17,0,10
0,0,3,0,-2066821056,22062,4,0,56,0,5,0,13,0,7,0,-243589120,32565,8,0,0,0,9,0,-2066816864,22062,11,0,1000,0,12,0,1000,0,1
3,0,1000,0,14,0,1000,0,23,0,0,0,25,0,1777555257,32765,26,0,2,0,31,0,1777561584,32765,15,0,1777555273,32765,0,0,0,0,-1832
560128,177746117,225241018,-794597185,909670636,3421791,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,It took me a while to understand the hint in the right way. 4+3+3-2 conversion required. means that provided numbers
are coded in octal notation.
I’ve decoded it.
octcode='67,66,40,66,71,40,67,63,40,66,70,40,67,67,40,66,61,40,64,63,40,65,64,40,64,66,40,67,142,40,65,65,40,65,146,' +\
'40,64,144,40,63,64,40,66,145,40,66,61,40,64,67,40,66,65,40,64,64,40,65,146,40,67,64,40,63,60,40,65,146,40,' +\
'66,144,40,63,60,40,64,64,40,63,61,40,66,66,40,65,71,40,65,71,40,65,71,40,65,146,40,65,67,40,63,63,40,66,' + \
'143,40,66,143,40,65,146,40,66,64,40,63,63,40,67,63,40,66,65,40,67,62,40,65,143,40,62,146,40,63,63,40,66,' + \
'64,40,67,144'
for i in octcode.split(','):
print(chr(int(i, 8)), end='')76 69 73 68 77 61 43 54 46 7b 55 5f 4d 34 6e 61 47 65 44 5f 74 30 5f 6d 30 44 31 66 59 59 59 5f 57 33 6c 6c 5f 64 33 73
65 72 5c 2f 33 64 7dOutput seems to be hexcode. So again…
echo -n 76 69 73 68 77 61 43 54 46 7b 55 5f 4d 34 6e 61 47 65 44 5f 74 30 5f 6d 30 44 31 66 59 59 59 5f 57 33 6c 6c 5f 64 33 73 65 72 5c 2f 33 64 7d | xxd -p -rvishwaCTF{U_M4naGeD_t0_m0D1fYYY_W3ll_d3ser\/3d}Flag
vishwaCTF{U_M4naGeD_t0_m0D1fYYY_W3ll_d3ser\/3d}